Advanced Security on Boomi using the Data Security Processor
Using Boomi Security Data Processor
I wanted to share a solution I developed to simplify Secured Operations around Symmetric and Asymmetric Cryptography and Digital Signature using Public Key Infrastructure with the Dell Boomi AtomSphere Platform. Dell Boomi Integration included out of the box Web of Trust functionality with PGP (Pretty Good Privacy) and this extension is adding:
- Support of X.509:
- For Signing and Signature validation
- For Encryption and Decryption
- Payload direct encryption/decryption
- S/MIME encryption/decryption
- Support of Javascript Object Signing and Encryption (JOSE):
- For JSON Web Signature (JWS) Signing and Signature validation, for standard text payload and Java Web Token (JWT)
- For JSON Web Encryption (JWE) Encryption and Decryption
The Boomi Security Processor will accelerate the Cryptographic operations and will wrap all the complex underlying operations:
-
Signing (Dell Boomi is the Sender on the following diagram) OR Validating Signature (Dell Boomi is the Receiver on the following diagram)
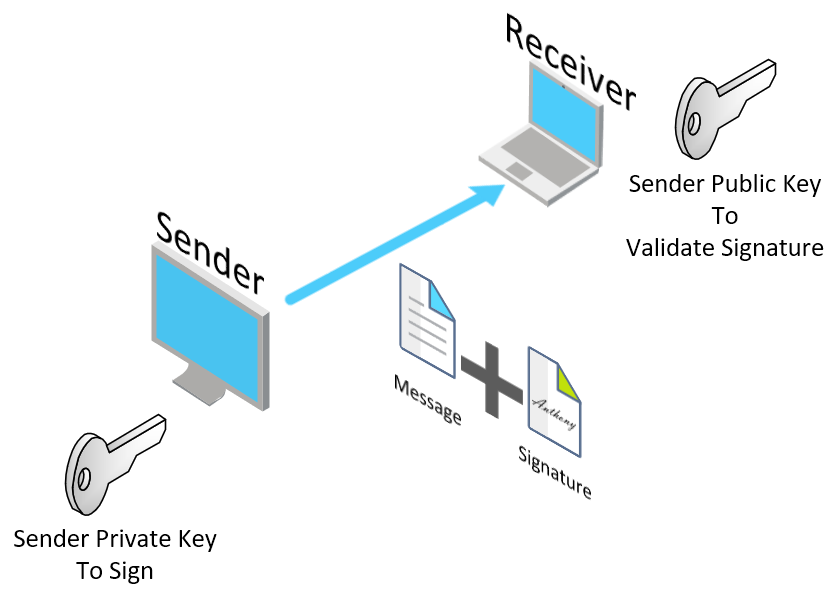
-
Encrypting (Dell Boomi is the Sender on the following diagram) OR Decrypting (Dell Boomi is the Receiver on the following diagram)
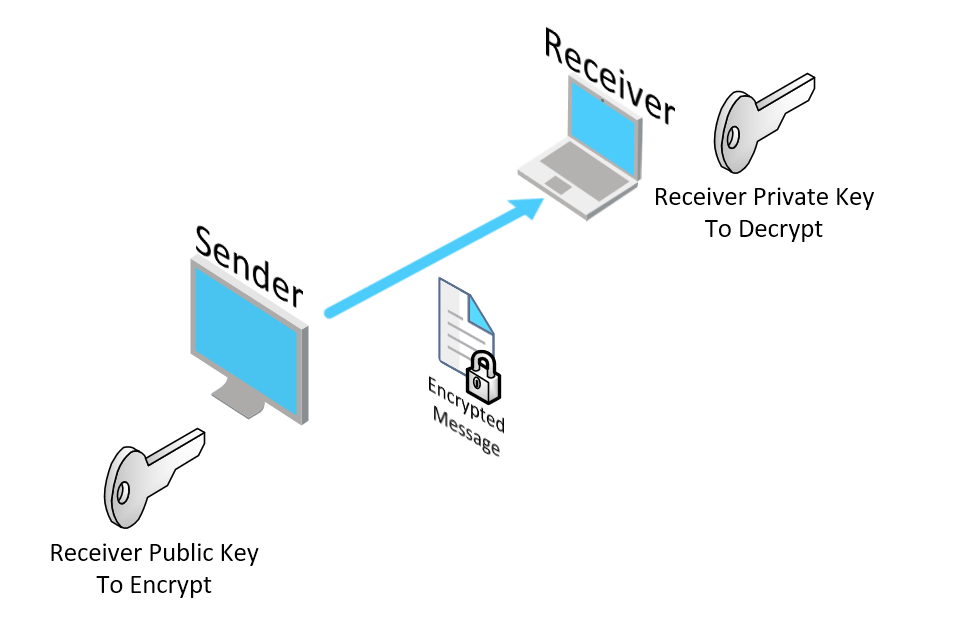
Exhaustive list of pre-configured Actions, Standards and Algorithms
| Actions | Standard | Algorithm |
|---|---|---|
| Sign or Validate Signature | X.509 | SHA1withDSA |
| X.509 | SHA1withRSA | |
| X.509 | SHA256withRSA | |
| Sign or Validate Signature | JWS | HS256 |
| JWS | HS384 | |
| JWS | HS512 | |
| JWS | RS256 | |
| JWS | RS384 | |
| JWS | RS512 | |
| JWS | ES256 | |
| JWS | ES384 | |
| JWS | ES512 | |
| Encrypt or Decrypt | X.509 | AES/CBC/NoPadding |
| X.509 | AES/CBC/PKCS5Padding | |
| X.509 | AES/ECB/NoPadding | |
| X.509 | AES/ECB/PKCS5Padding | |
| X.509 | DES/CBC/NoPadding | |
| X.509 | DES/CBC/PKCS5Padding | |
| X.509 | DES/ECB/NoPadding | |
| X.509 | DES/ECB/PKCS5Padding | |
| X.509 | DESede/CBC/NoPadding | |
| X.509 | DESede/CBC/PKCS5Padding | |
| X.509 | DESede/ECB/NoPadding | |
| X.509 | DESede/ECB/PKCS5Padding | |
| X.509 | RSA/ECB/PKCS1Padding | |
| X.509 | RSA/ECB/OAEPWithSHA-1AndMGF1Padding | |
| X.509 | RSA/ECB/OAEPWithSHA-256AndMGF1Padding | |
| Encrypt or Decrypt | JWE | A128CBC-HS256 |
| JWE | A192CBC-HS384 | |
| JWE | A256CBC-HS512 | |
| JWE | A128GCM | |
| JWE | A192GCM | |
| JWE | A256GCM | |
| Encrypt or Decrypt | S/MIME | TRIPLEDES |
| S/MIME | DES | |
| S/MIME | RC_2_128 | |
| S/MIME | RC_2_64 | |
| S/MIME | RC_2_40 | |
| S/MIME | AES_128 | |
| S/MIME | AES_192 | |
| S/MIME | AES_256 |
Getting Started
Please download the library connector-archive and the connector descriptor connector-descriptor.
Prerequisites in Boomi
Setup of the Connector
Please go to Setup>Account>Publisher and fill out the information.
And then, go to Setup>Development Resources>Developer and create a new Group. The two files to upload are the files you previous downloaded. For the Vendor Product Version, please mentioned the version of the Zip Archive.
Use of the Connector
The configuration is done by configuring the Connector (name Data Security Processor in the following capture):
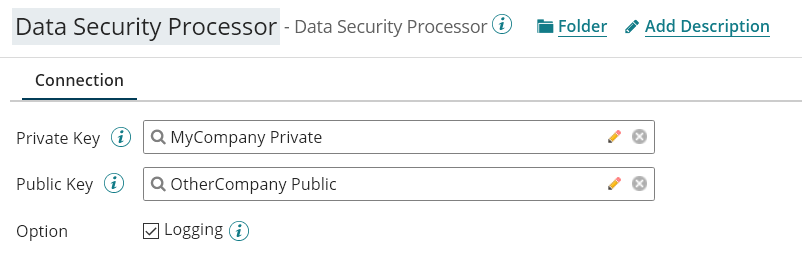
The Private and Public keys are standard Boomi Certificate created using:
- p12 or pfx file for Private Key
- cer or der for Public Key
Once the Connector configured, create an execute operation with one of the four operations:
- Sign
- Validate Signature
- Encrypt
- Decrypt
Implementing Processes with the Security Data Processor
Signing
The Following Process is the process using the Sign Operation:
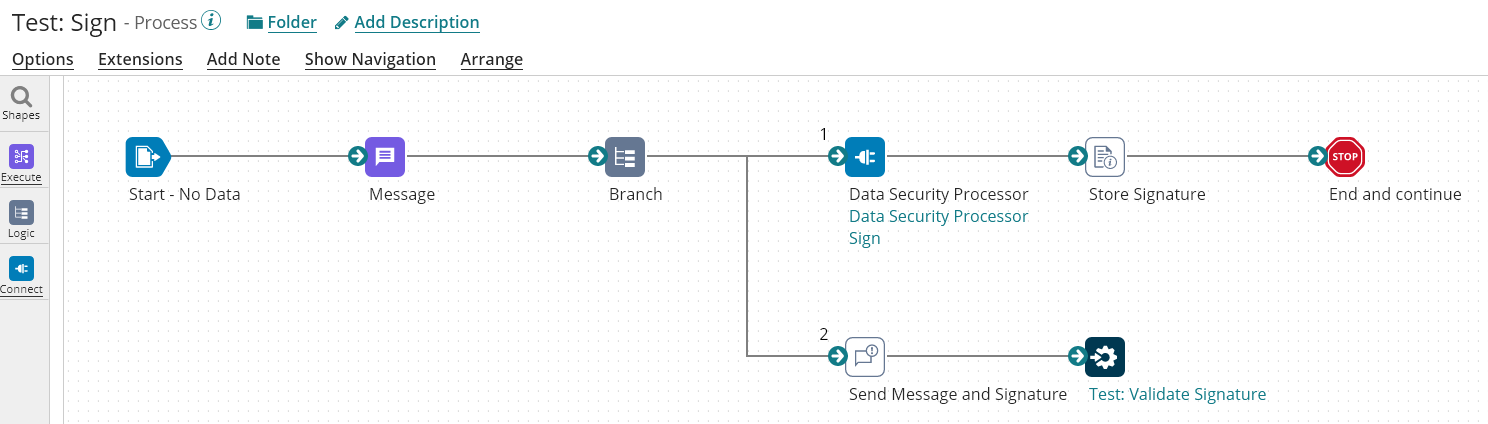
The Operation is configured as follow:
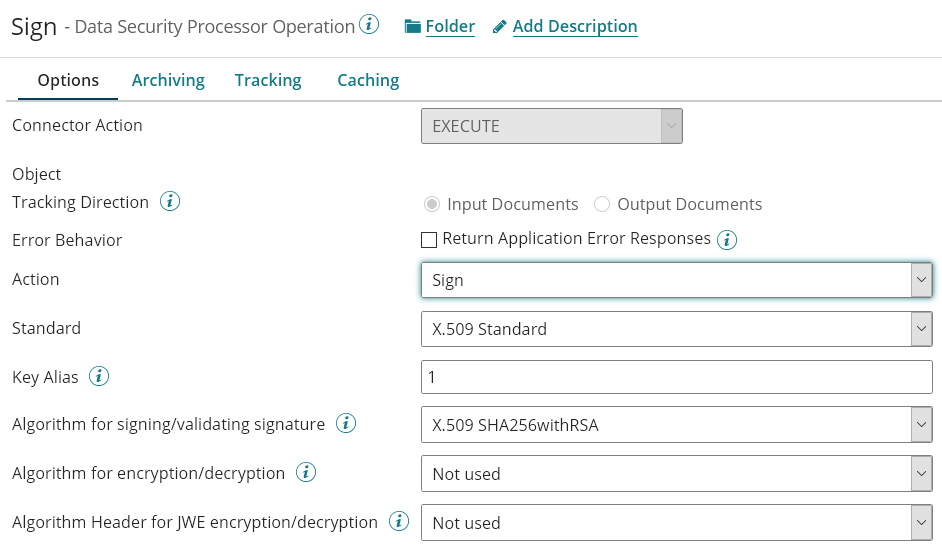
Validating Signature
The Following Process is the process using the Validate Signature Operation:
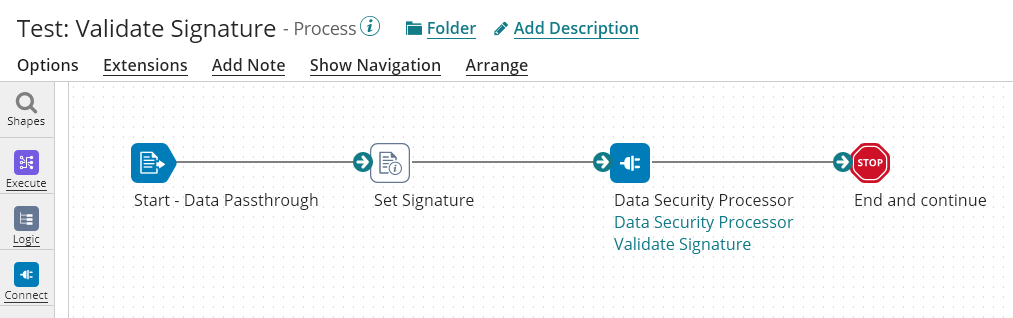
The Set Signature uses the following Document Property of the connector:
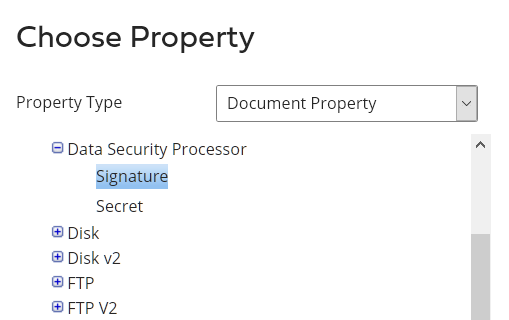
The Operation is configured as follow:
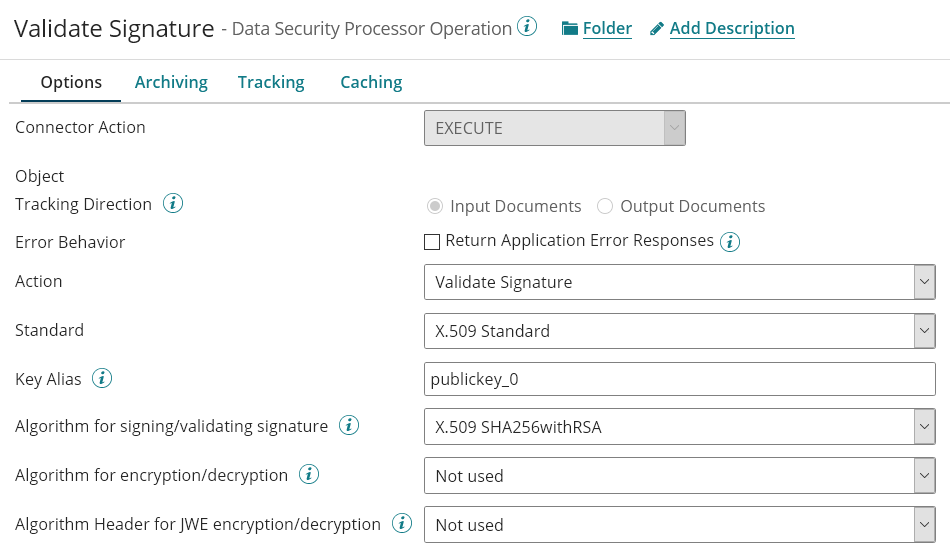
The output document will be a boolean providing the validity of the signature:

Validating Signature of a Java Web Token (JWT)
The Following Process is the process using the Validate Signature Operation:
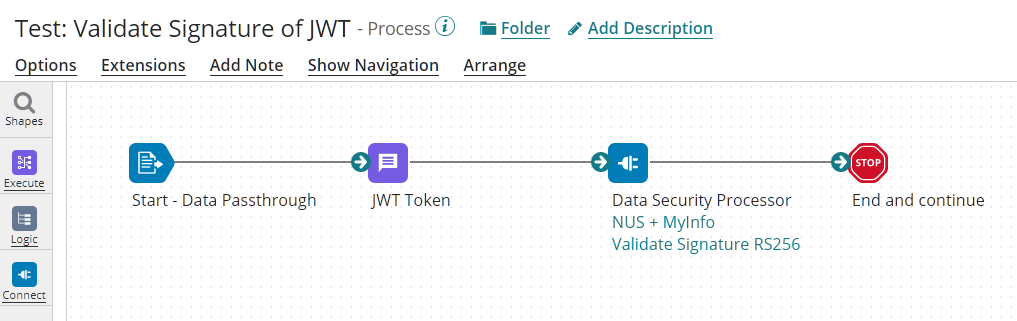
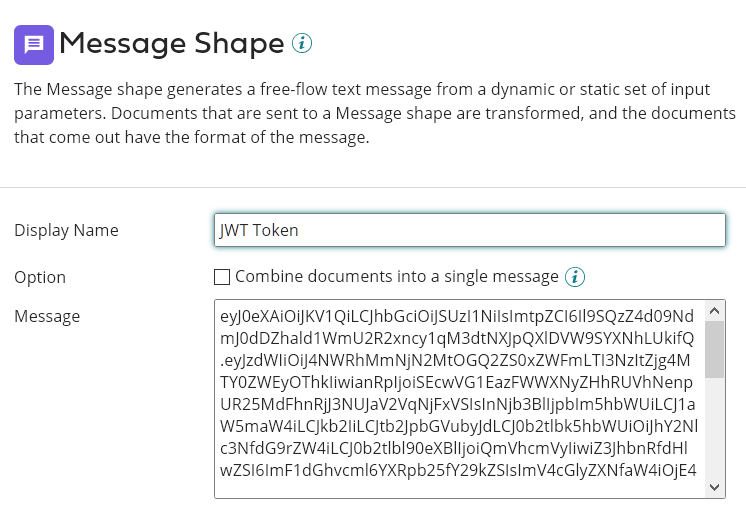
The document in this example is defined as a Message and contained the full JWT Token (with multiple dots):
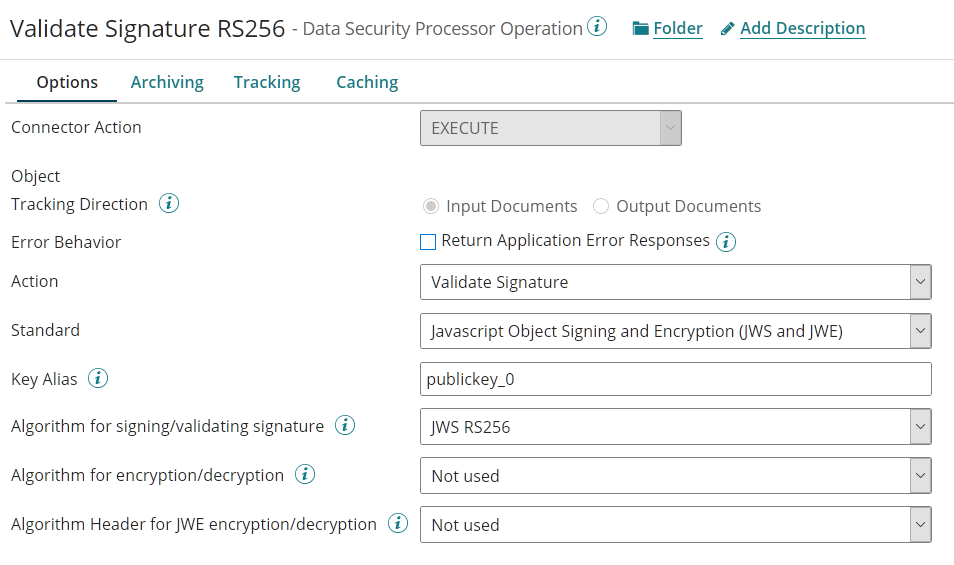
The Operation is configured as follow:
The output document will be a boolean providing the validity of the signature:

Encrypting
The Following Process is the process using the Encrypt Operation:
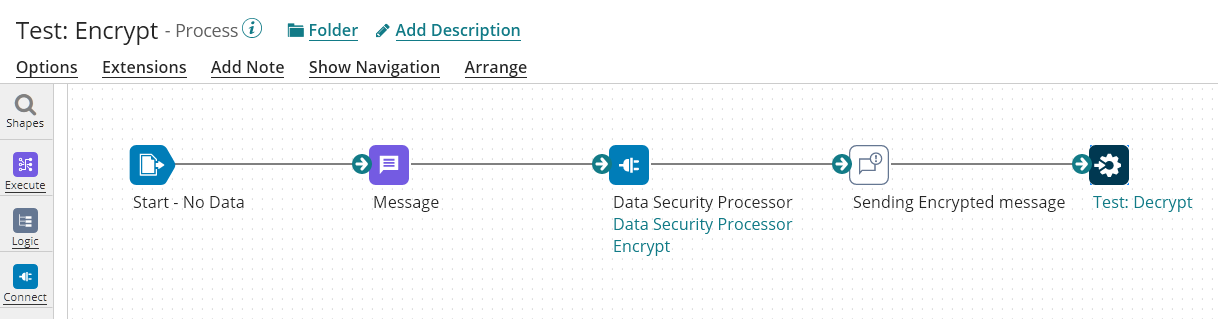
The Operation is configured as follow:
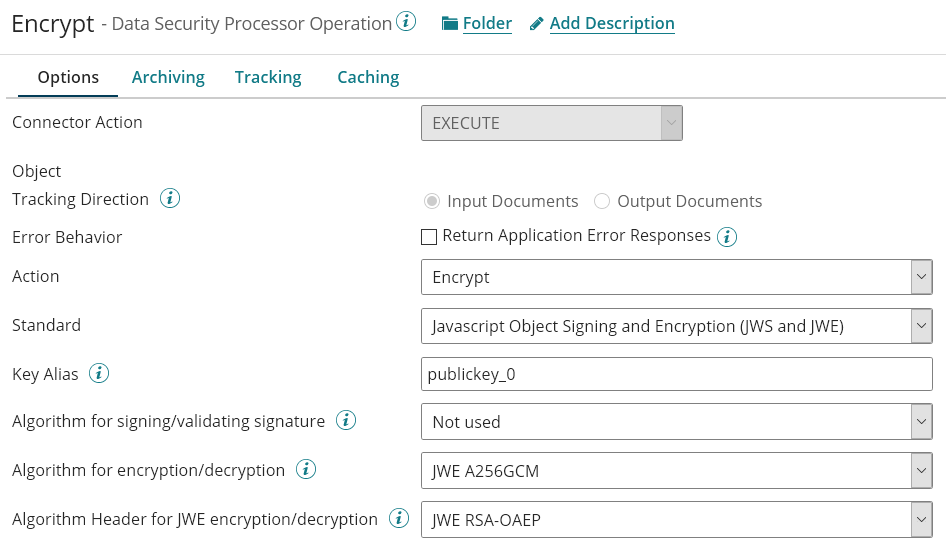
Decrypting
The Following Process is the process using the Decrypt Operation:
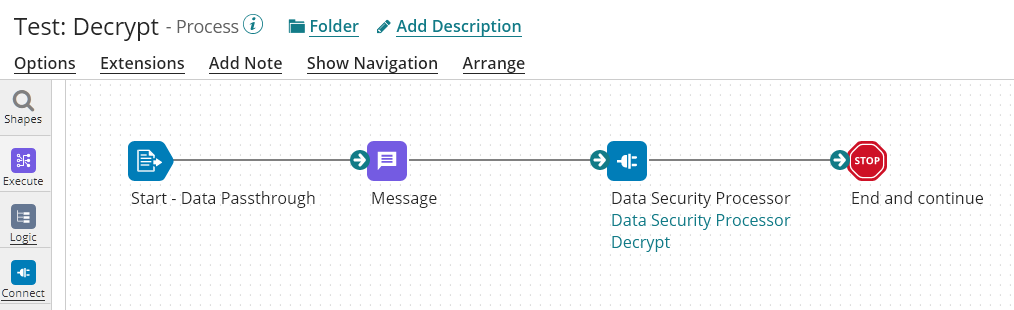
The Operation is configured as follow:
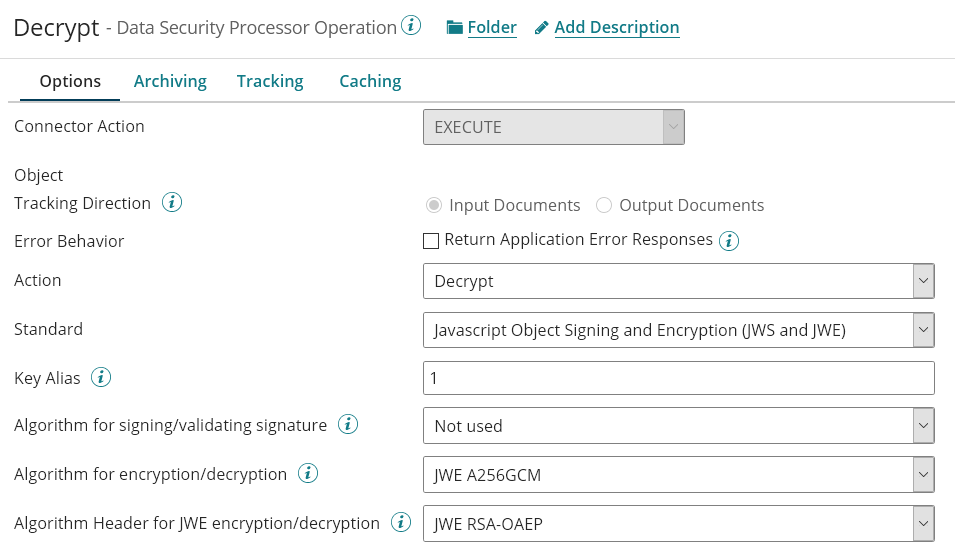
Implementing fields encryption/decryption in Map
We can use the Get operation of Security Processor to encrypt and decrypt fields with Salting (put 0 for the value of salt size to disable salting).
Creation of the Security Operation
Create a new Connector Operation with “GET” type and click on “Import”
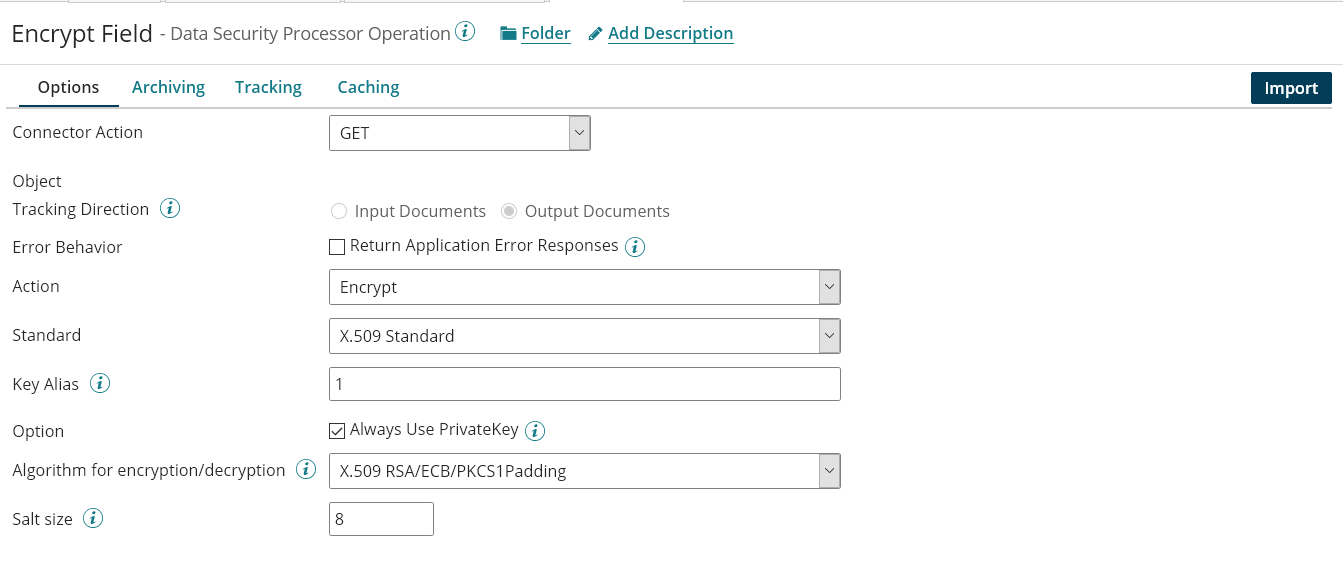
Select the object type (here Get_Encrypt)
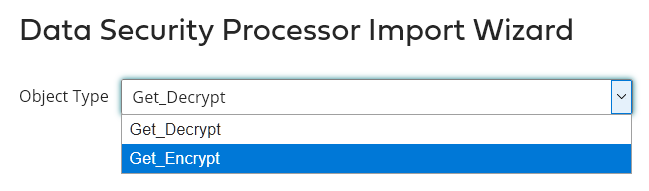
Click on Next
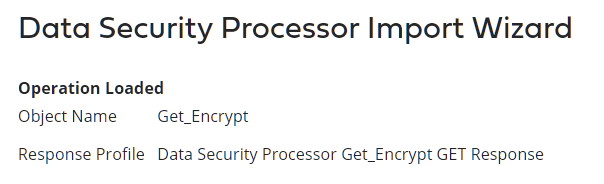
Validate that the Response Profile is created and make sure that its type is Get_Encrypt if Action = Encrypt.
For Action = Decrypt, please use Get_Decrypt object during the import.
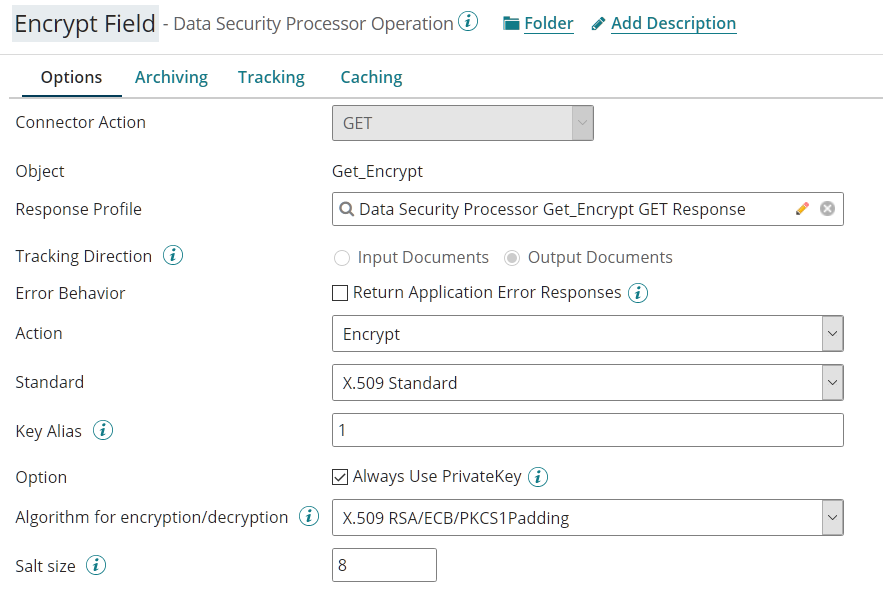
Operation Key Alias
The value for Key Alias is the alias name of the entry value from the Private or Private Key.
There are multiple ways to get this value.
- Using keytool
keytool -v -list -keystore boomi.pfx
Enter keystore password:
Keystore type: PKCS12
Keystore provider: SUN
Your keystore contains 1 entry
Alias name: 1
- Using keystore explorer
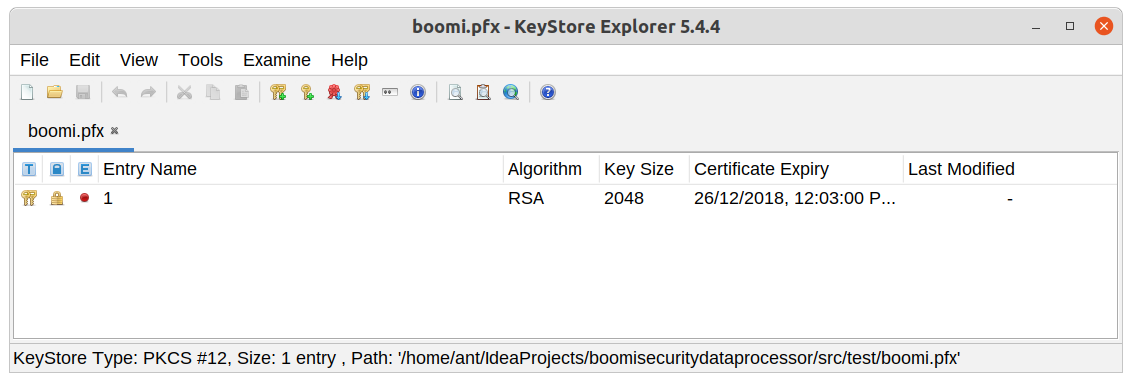
In our case, we have to put 1 as Key Alias.
For public key, use the value: publickey_0
Map with field encryption
In your Map shape:
- add a function
- select Connector Call
- use the existing Connection
- select the previous created Operation
- on Input, select ID
- on Output, select the corresponding object (encryptedValue or decryptedValue)
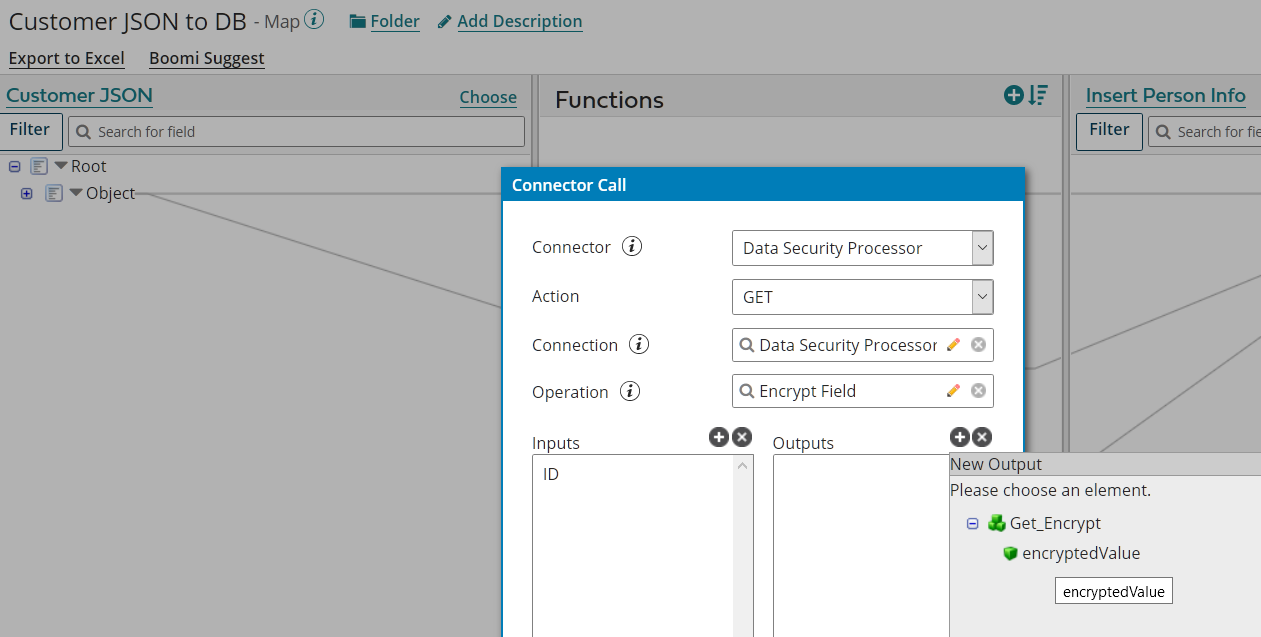
Validate the input and output of the Function
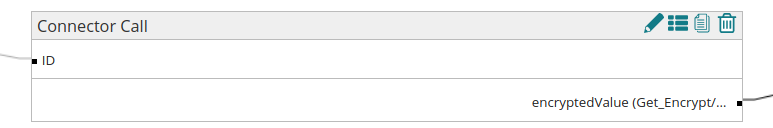
Overall Process using the map with field encryption
Example of process reading values in JSON and writing to a DB
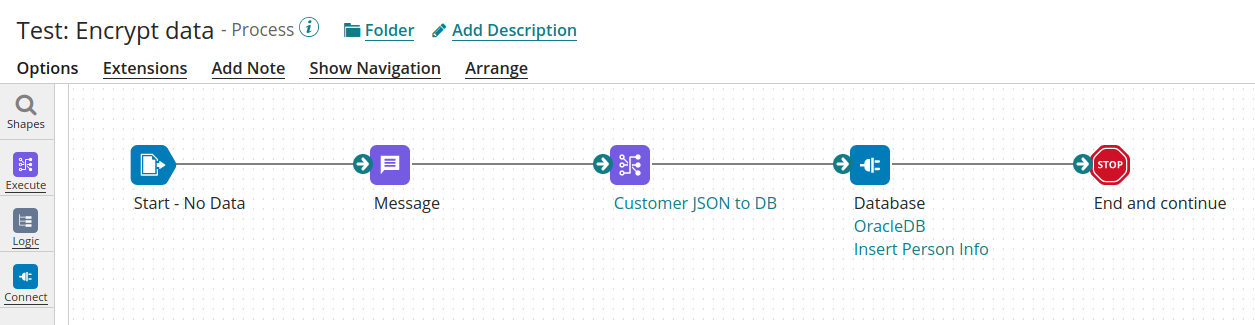
Output in the DB , please make sure that the size of the column is wide enough (in our example a field of 16 chars + salt of 8 chars is converted to a string of 344 chars)
Access to the source code
Go to GitHub to get the latest version of the zip and the XML descriptor